- The Decision Diffie-Hellman problem. D. Boneh, ANTS 3, 1998
Talks about various assumptions related to Diffie Hellman. - Universal Hash Proofs and a Paradigm for Adaptive Chosen Ciphertext Secure Public-Key Encryption. R. Cramer and V. Shoup, Eurocrypt 2002
- Chosen-Ciphertext Security from Identity-Based Encryption. D. Boneh, R. Canetti, S. Halevi, and J. Katz, SICOMP 2007
Uses a general mechanism called Identity Based Encryption which very surprisingly it turns out to actually gives us chosen ciphertext security almost for free. - The Twin Diffie-Hellman Problem and Applications David Cash1 Eike Kiltz2 Victor Shoup3
- Efficient Chosen-Ciphertext Security via Extractable Hash Proofs Hoeteck Wee?
Gives a very general framework for building chosen ciphertext ciphertext secure systems using extractable hash proofs.
一些关于 RSA 的 paper
- Who chosen ciphertext security matters, V.Shoup, 1998
A nice paper by Victor Shoup that talks about why chosen cipher text security is so important in the public key settings. So if the Bleichenbacher attack wasn’t convincing enough, there are many other attacks like this that are possible if you don’t use a chosen cipher-text secure system. - Twenty years of attacks on the RSA cryptosystem, D.Boneh, Notices of the AMS, 1999
- OAEP reconsidered, V.Shoup, Crypto 2001
- Key length, A.Lenstra, 2004
A nice paper by Arjen Lenstra that discusses how you should choose key lengths for your public key systems, and even for your symmetric key systems.
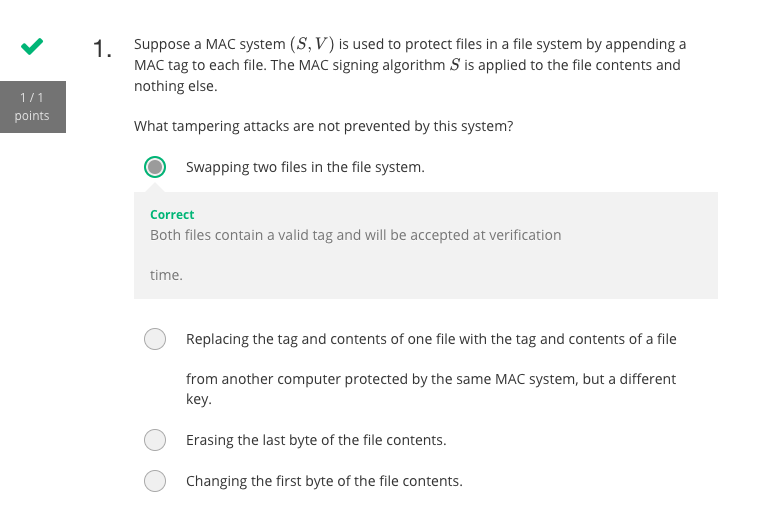
Cryptography Week 5 - Programming Assignment
Cryptography Week 5 - Problem Set
Proof of Fermat's Little Theorem
新专栏:数论
一个新的专栏: Fun with number theory。这个专栏将从费马小定律开始,讲一些简单的数论知识,并介绍这些数论知识在公钥密码学、素数检查、复数计算等方面的应用
由于本人也是初学者,错误及遗漏之处还请大家多多指正
Vim Lisp Plugin 推荐
使用 lisp 编程的时候括号是一个很让人头疼的问题,vim 自带的 matchparen 可以起到一定的帮助,但是还是有两个小问题:
- 需要将光标移到括号上才能知道它对应的是哪个括号
- 频繁报错,很影响编码效率
在这里向大家推荐两个插件帮大家更舒服地编写 lisp
一些关于 Key Exchange Protocol 的 paper
- Mer Puzzles are Optimal, B.Barak, M.Mahmoody-Ghidary, Crypto ‘09
当我们只使用 symmetric ciphers 和 hash functions 的时候,Merkle Puzzles 是 key exchange 的最优选择。即我们无法在这样的限制下超越 quadratic gap - On Formal models of key exchange (sections 7-9) V.Shoup, 1999
Closed Form Expression For Fibonacci Numbers 的证明
Counting Change 问题的详细分析及解答
SICP 学习环境的搭建
Cryptography Week 4 - Programming Assignment
这次我们的目标是利用 Padding oracle attack 破解加密过的消息,padding oracle attack 的原理相对来讲比较简单,但是在具体的编程破解过程中需要注意几个问题:
- 发送 chosen ciphertext 的间隔时间不能太短,不然会收到 500 响应
- 在第一个字节被成功 decrypt 之后,可根据 padding 格式跳过一些字节,节省一些时间
Cryptography Week 4 - Problem Set
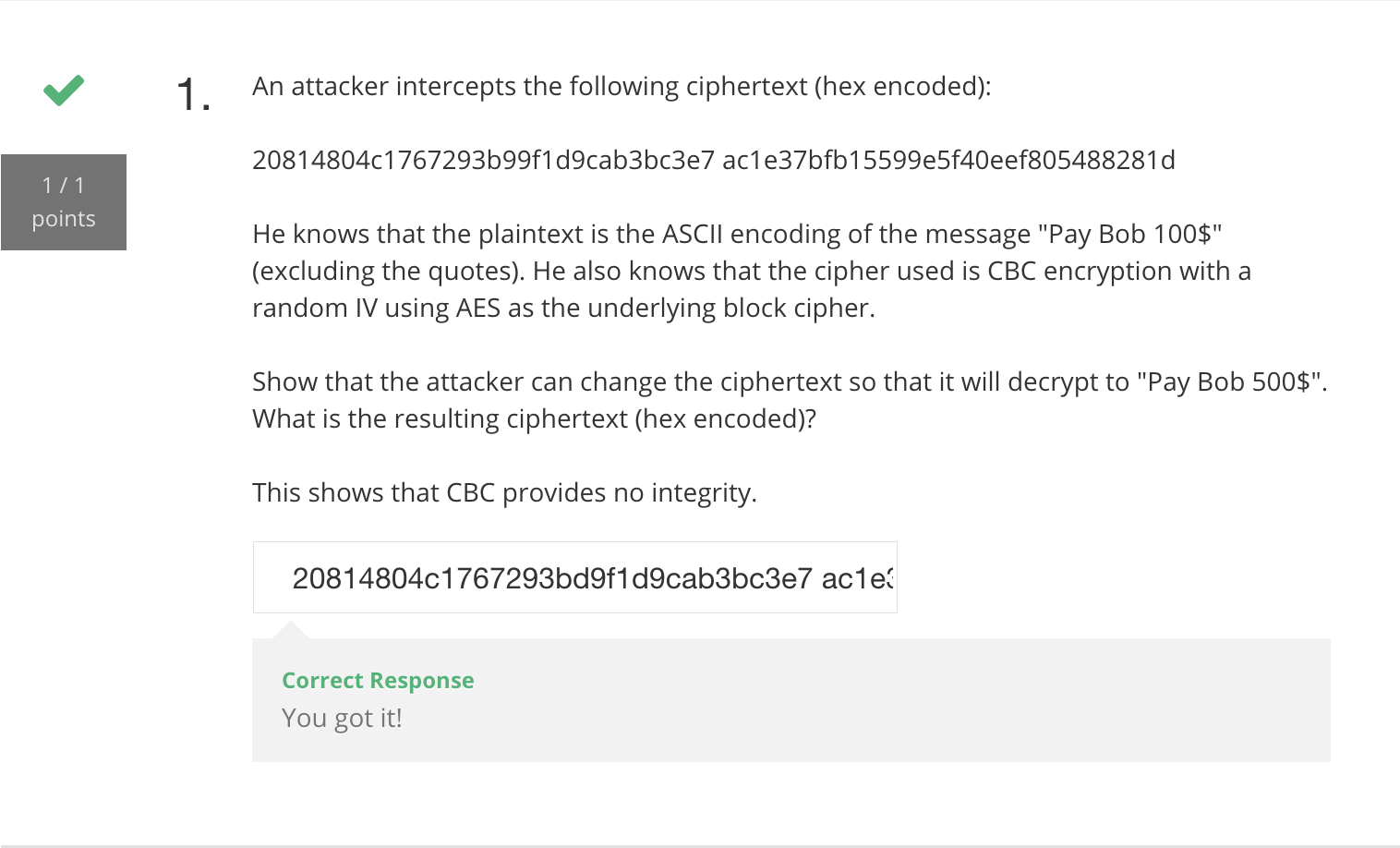
我们可以从 Padding oracle attack 中找到伪造密文的思路:
设:$1 \oplus x = 5$, IV 中的对应字节为 $y$
则:当 $y’ = y \oplus x$ 时,$y \oplus 1 \equiv y’ \oplus 5$
所以:将 $y$ 更改为 $y’$ 可使 message 中的相应字节变更为 5
Cryptography Week 3 - Programming Assignment
本周的任务是实现对大文件的分块哈希,使得浏览器可以在仅收到一部分文件的时候进行 MAC 校验(假设初始 MAC 已通过可信赖的途径分发给浏览器)
一些关于 MAC 的 paper
- J.Bloack, P.Rogaway: CBC MACs for Arbitray-Length Messages: The Three-Key Constructions. J.Cryptology 18(2):111-131 (2005)
讲了 CMAC 的基础构型:three key construction - K.Pietrzak: A Tight Bound for EMAC. ICALP (2) 2006: 168-179
证明了 CBC-MAC 的超集是 PRF
Cryptography Week 2 - Programming Assignment
这次我们的任务是实现 CBC 和 CTR,要求用 AES 做为 PRF,所以我们只需要使用 AES 的加密算法。